Being an expat with multiple bank accounts in different countries, and important documents such as passports, visas, life insurance and other contracts I seem to have amassed a huge collection of important but private information which is essential to the smooth running of my life. Whatever the documents maybe if you’re like me then keeping track of it all is a headache made even it’s made even more complex as conventionally it’s a bad idea to store it all in the same place which would make identity theft much easier if that information was compromised (i.e. stolen). Added to this you need this information to be easily accessible as it would be pretty difficult to memorize it all (e.g. online bank credentials, emergency contact and policy numbers etc).
So what’s the solution for keeping your personal information secure but accessible at the same time?
One solution I’ve found which works well is to use a combination of the cloud storage service Dropbox and disk encryption software TrueCrypt:
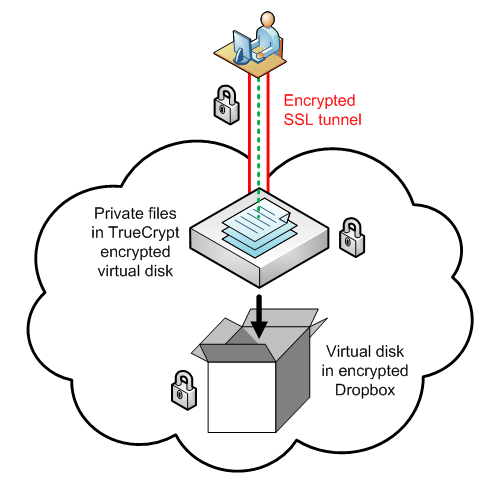
Whilst this might look a bit daunting it’s simpler than it appears. TrueCrypt allows you to create a virtual encrypted disk within a file which can be mounted on your computer as an ordinary disk (like plugging in a USB drive). Dropbox allows you to sync your files online (in the “cloud”) and across multiple computers.
The basic step for setting this up are as follows:
- Sign up for a Dropbox account & install the client (2GB of storage free, works on all platforms)
- Download and install TrueCrypt (opensource, works on all platforms)
- Run the TrueCrypt Volume Creation Wizard to create a new virtual encrypted disk within a file (default option). When selecting the volume size be sure to keep it <5MB depending on your internet connection speed as this will have to be updated each time you unmount (disconnect) the disk.
- Save the virtual disk file to your Dropbox (usually within My Documents on Windows or your Home Directory on Mac OS/Linux).
- Place your secret files within the virtual disk and mount/unmount as needed.
Dropbox encrypts all files with AES-256 before being sent to their servers over an SSL connection (similar to when you make a credit card purchase online). Combined with TrueCrypt this essentially “triple encrypts” your files so in the extremely unlikely event that someone compromised the Dropbox servers or your computer then your files would still remain safe.
There are other all-in-one solutions which do similar things (like 1Password) but the problem I have with these is that you’re still entrusting your security to other people and most are platform-dependent. With this solution, you have multiple levels of protection and you’re still in complete control.
While this works quite well for me there may be better methods so if you know of one please leave a comment below!

Reply